Supply chain security | KubeCon India
It’s not new that supply chain security is the talk of the town, with tools popping up every now and then to make sense of SBOMs and achieve SLSA compliance.
SLSA, or Supply-chain Levels for Software Artifacts ("salsa"), is an industry standard for protecting against supply chain threats. Various levels are defined, with the current focus of SLSA being on the build track within the entire chain, though work is also ongoing in parallel tracks, such as the source track.
As you can see from the image (taken from the official SLSA website), software goes through various stages, and at each stage, there is a different set of potential attacks, as illustrated below.
These attacks are well-known, and new ones keep emerging, so it’s not a one-time occurrence—it’s been happening and is accelerating.
To prevent this, various tools are in place, and one particular framework worth mentioning is the SLSA framework and its levels.
As mentioned before, there are various SLSA levels, and Level 0 essentially means that nothing is being done for your builds, with builds happening directly from laptops and no CI/CD pipelines in place.
Level 1 means the build process is documented, and a provenance is being generated. To understand this from a real-world perspective, an SBOM is like the ingredient list for preparing a dish, and provenance is like the recipe. There are tools available for this, such as Docker, which provides commands for generating provenance during the build process.
docker buildx build --tag <namespace>:<image>:<version> --attest type=provenance,mode=[min,max] .Level 2 - This suggests that builds should not happen from your laptops but instead on a centralized platform that generates and signs provenance. The provenance should then be published to allow downstream users to verify it. For example, platforms like GitHub Actions can help you achieve this.
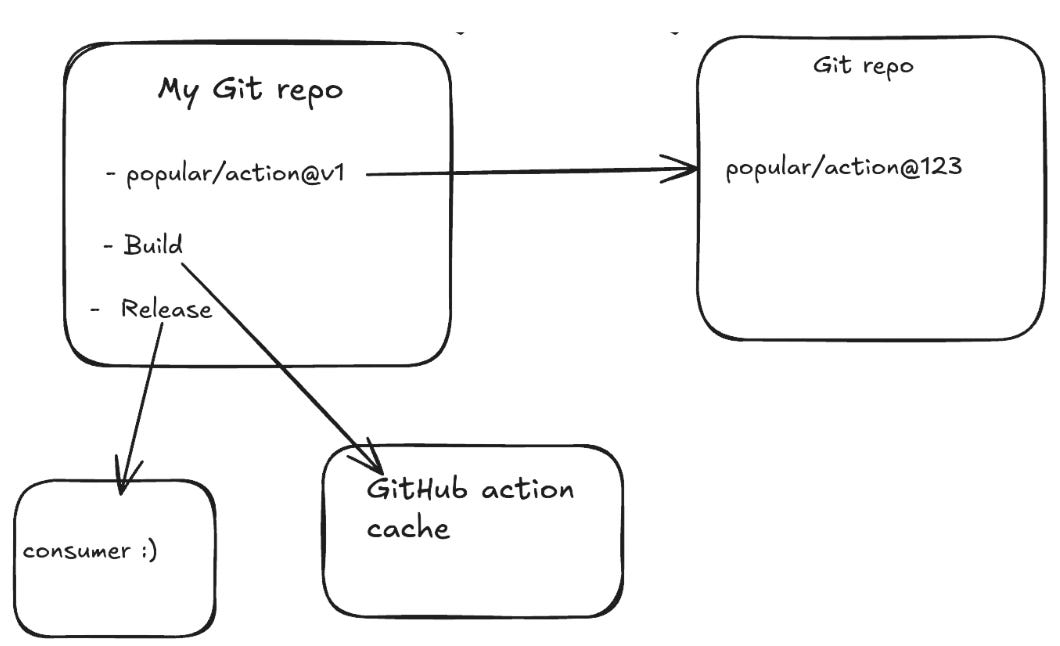
Level 3 - This level focuses on creating a secure build platform to ensure that build runs do not influence each other (e.g., cache poisoning) and implementing secure secret management on the build platform. Cache poisoning can be better understood with the screenshot below, which demonstrates how an attacker can poison a repository used in GitHub Actions, ultimately leading to the end user also being attacked.
Level 3 and beyond is particularly interesting because we cannot definitively say GitHub Actions is Level 3, and while Docker Build can be Level 3, it’s not straightforward to implement.
This is where BuildSafe comes in, helping you create zero/low CVE base images and enabling hermetic builds along with reproducible builds, both of which are essential.
Hermetic Builds: The build process and resulting artifacts are unaffected by external influences. Every build step, input (i.e., source code), and dependency must be declared using a reference that identifies a unique, immutable artifact.
Reproducible Builds: A build process is reproducible if, given the same build definition, comprising immutable and verifiable references to build steps, source code, and dependencies, it consistently produces an identical result.
We have an end-to-end demo in the BuildSafe repository that demonstrates hermetic builds in action. Achieving SLSA compliance is something everyone should strive for.
On another note, KubeCon India was held for the first time in Delhi at Yashobhoomi, and it was an incredible event! I had a great experience meeting everyone in person, especially those who came up to thank me for the content we create for Kubesimplify. It was overall a fantastic experience, and we recorded some interviews to showcase the amazing turnout at the event.
I also gave a talk at the SOSS Community Days on BuildSafe and on cell-based architecture in Kubernetes, showcasing a demo using vCluster. The talks will soon be available on the LF and CNCF YouTube channels, and I’m excited about the introduction of LF India!
While I haven’t been able to create much content for Kubesimplify lately, after KubeCon India, I’ll be doubling down. Expect lots of surprises ahead! First, I’ll be completing the CKS series, followed by massive new courses, everything will be top quality and the best in the industry, as always.
Reading Awesome stuff
I have been reading bunch of things while travelling
Kubernetes v1.32: Penelope - Kubernetes v1.32, themed "Penelope," marks a significant milestone with 44 enhancements, including 13 features graduating to Stable, such as structured authorization and memory-backed volume sizing, alongside new alpha features like asynchronous preemption and mutating admission policies. The release reflects a decade of Kubernetes evolution, emphasizing improved resource management, operational resilience, and usability, while showcasing robust community contributions and plans for ongoing development and ecosystem expansion.
Kubernetes v1.32: Memory Manager Goes GA - With Kubernetes v1.32, the memory manager has graduated to General Availability (GA), enabling efficient and predictable memory allocation for containerized applications in the Guaranteed QoS class. This milestone brings improved observability, reliability, and robustness, with future plans to extend support to Windows for enhanced CPU and memory affinity.
Salesforce Preps Heroku PaaS for Kubernetes Environments - Salesforce's Heroku PaaS now runs natively on Kubernetes, integrating with AWS services, supporting OCI specifications, OpenTelemetry, and adding .NET language support alongside existing options. By simplifying infrastructure complexities, Heroku aims to accelerate cloud-native application development and aligns with the growing trend of platform engineering for standardization and productivity.
Introducing Supply-Chain Firewall: Protecting Developers from Malicious Open Source Packages - Datadog Security Labs has introduced Supply-Chain Firewall, an open-source tool designed to protect developers from malicious and vulnerable packages on PyPI and npm by blocking or flagging risky installations. This Python-based solution offers developers enhanced security for their workstations, integrates seamlessly with tools like Datadog Log Management for observability, and is poised for further expansion to support additional package managers and community contributions.
When Kubernetes Fails: Reflections on the OpenAI Outage - The recent OpenAI outage, caused by a telemetry stack deployment in their Kubernetes environment, highlights the platform's operational complexity even for experts, as it disrupted their control-plane access and required significant recovery efforts. This serves as a wake-up call for organizations, emphasizing the need for Kubernetes expertise, proactive safeguards, and simplified management solutions like Portainer to mitigate risks and make Kubernetes more accessible to smaller teams.
Devin is now generally available - Devin, an AI development assistant now available at $500 per month, streamlines engineering tasks with features like Slack integration, an IDE extension, and API access. It excels in handling bugs, PRs, and refactoring, with proven contributions to open-source projects like Anthropic MCP and Zod, showcasing its effectiveness with human guidance.
Awesome Repo’s
usernetes - Kubernetes without the root privileges
If you like reading the awesome newsletter, please do subscribe for free and share within your network.